Frameworks for Cyber Success
Cyber continues to lag in mission driven spaces.
I read a few stats from Diligent this morning that reminded me just how much cybersecurity matters in the mission driven and nonprofit space.
Here are a few from their "Key Stats that Boards Need to Know:"
50% of NGOs reported cyberattacks in 2021
NGOs and Nonprofits raise $30 BILLION each year
Only 25% of nonprofits monitor their networks
Only 20% have a cybersecurity plan
Clearly there is more need than the cyber industry is able to provide for!
Let's get into the weeds a bit on how Ericius Security helps fix this.
Frameworks for success
There are a number of good cybersecurity frameworks for organizing defenses and IT risk management. The CIS Critical Security Controls and ASD Essential 8 are popular, but I tend to lean on the National Institute of Standards and Technology's Cyber Security Framework (CSF) crossed with the Cyber Defense Matrix (CDM) by Sounil Yu.
Why? The CSF is free. You can use it commercially, so you can apply it to your business. And it's thorough enough to handle organizations of all maturity levels.
I cross it with the CDM to standardize the application of the CSF's functions across all types of IT assets, as well as to get a FAST representation of where a business's cyber program is at--two things that the CDM was specifically designed to do and does EXCEPTIONALLY well.
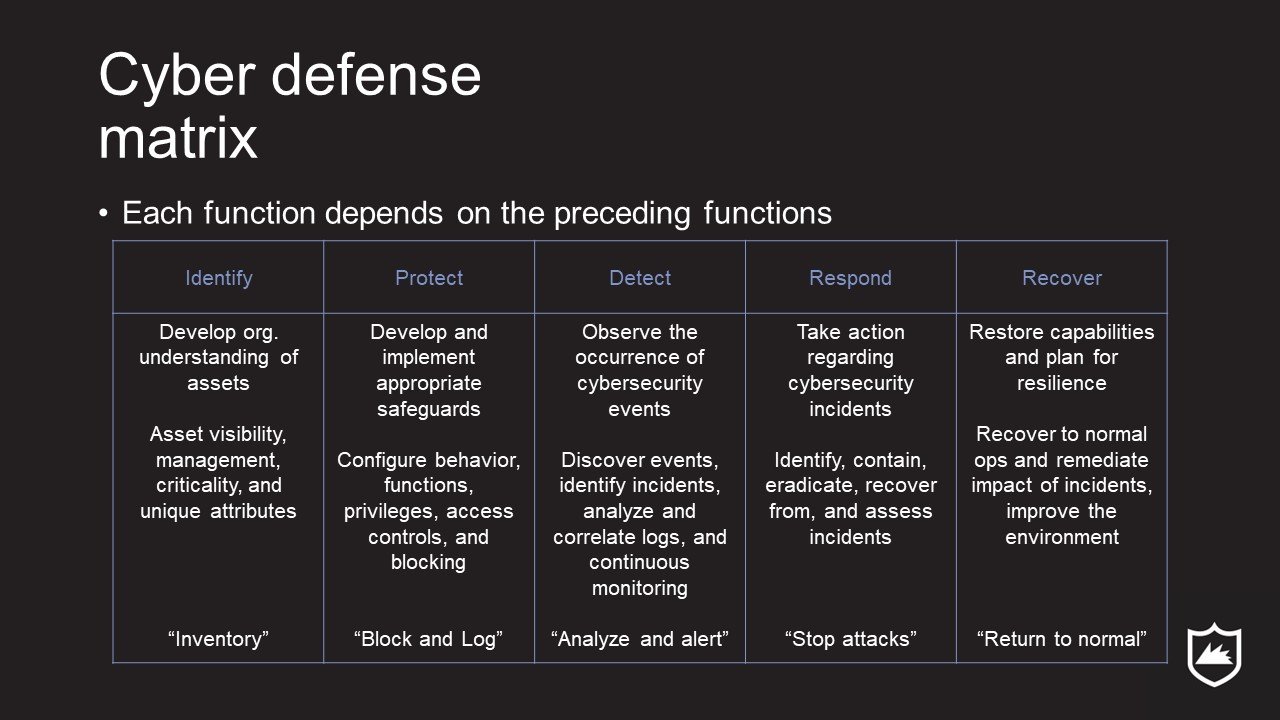
The CSF Provides the functions:
The five functions of the NIST Cyber Security Framework
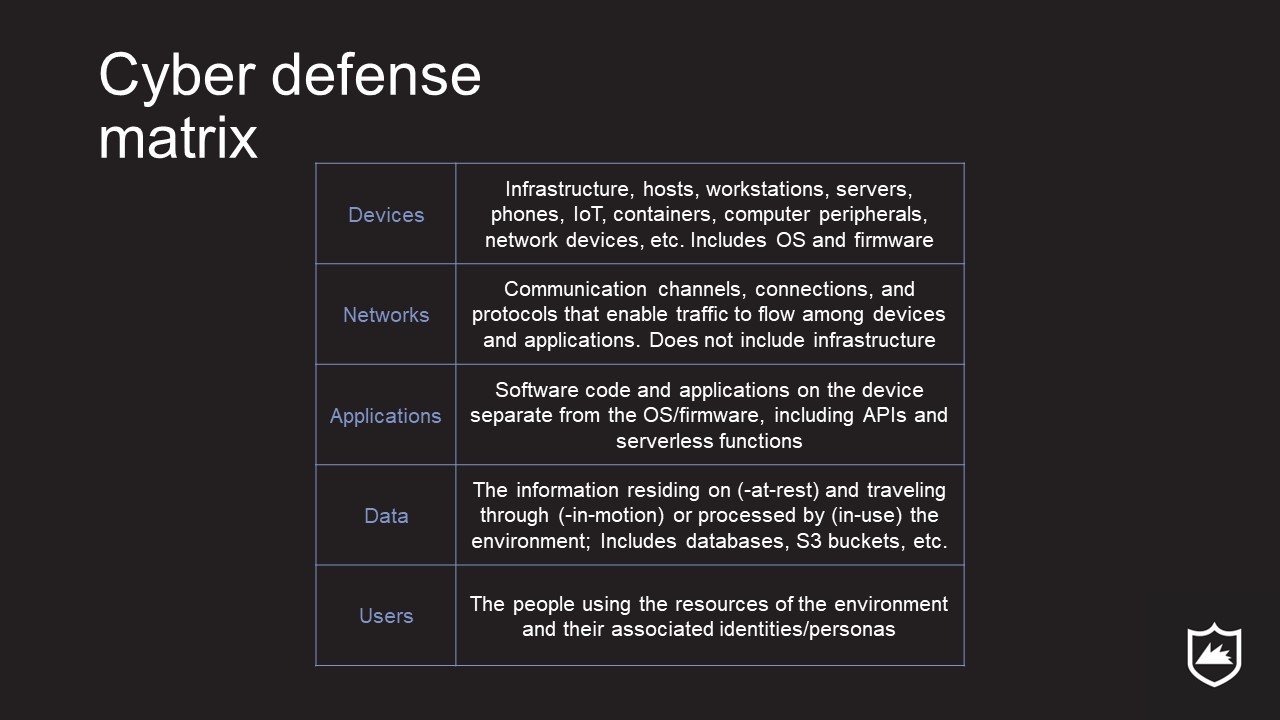
The CDM standardizes the functions across five assets:
The five asset classes as defined in The Cyber Defense Matrix by Sounil Yu
The resulting matrix allows us to produce a high-level view of the security program.
The cyber defense matrix
Here's how it works when I run it:
Discovery - We talk through the business's goals followed by everything in the existing IT environment. What needs defending? How many users are there? How are finances supporting the mission? Where are the pain points?
Map Current State - We map the existing defensive capabilities onto the CDM
The current state maps your existing cybersecurity capabilities to the cyber defense matrix
Map Desired State - We map the business's goals onto the CDM and define requirements, then we provide some professional insight about noticeable gaps, opportunities for improvement, and places where complexity can be reduced
The desired state overlays new cybersecurity capabilities on existing capabilities
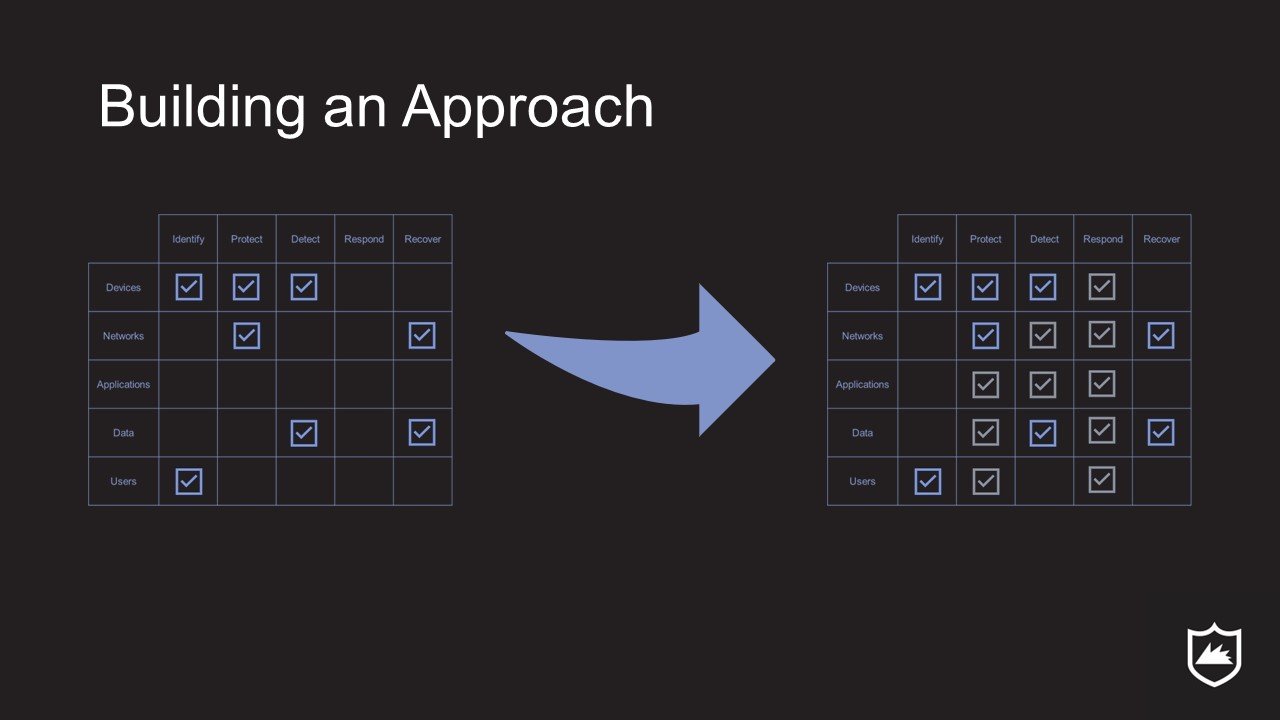
Develop an Approach - We design a 3 steps bridge from the current state to desired state that the business can execute over the next year
The approach moves the current state to the desired state
Afterwards, we can either search for managed security services to fill gaps with the business, or we can do more detailed analysis, consulting, and program building--perhaps policies need to be written or a three year roadmap for growth needs to be designed.
If that sounds helpful to you or to a mission driven business you know, we've wrapped this all up in a DIY version that you can find here or you can always book a call to get help.