Why cybersecurity and nonprofits?
Ericius Security builds cybersecurity programs where they don’t exist, and we specialize in high-risk nonprofits.
Why cybersecurity and nonprofits? The short answer is that cyberattacks effect people. When computers are under attack, people are under attack.
The long answer is that cybersecurity should be part of your overall risk management and operations security efforts. These efforts are about mission success, good stewardship, and safety.
Cybersecurity contributes to mission success in a variety of ways. The most obvious way is that it allows you to retain control of your digital assets and use them the way they were created to be used. It also supports success in more subtle ways, such as protecting trust between your team members when they are communicating by providing ways to verify people are who they claim to be.
Risk management and security may seem like they distract from the mission—they’re simply overhead. But in reality, they are part of good stewardship. When people donate to a cause they want to see their money go as far as possible to create a positive impact on the world. You aren’t stewarding money well if you leave what you have unprotected for thieves. Investment in cybersecurity can prevent predictable problems and lessen losses. It’s still technically overhead, but it’s less overhead than the chronic costs and loss of trust stemming from breach.
Finally, cybersecurity supports member safety and care. Good security efforts can actually help reduce the sense of fear and paranoia your team may face by giving them a calibrated sense of what actually might go wrong (and what probably won’t go wrong). That tangibly reduces stress. It also shows your team you’re resourcing them and are concerned about their safety. It’s also a safety feature because it helps you retain control over information. We tend to think about cybersecurity and critical information in terms of reducing identity theft and fraud, but it can also help protect the locations of safe houses, the names of sources, and the nature of high risk/reward efforts.
People tend to decide cybersecurity is worth considering at different times during the life of their missions and businesses, but most commonly they’re either preparing to go work in place particularly well known for cyber-crime, are just recovering from a breach and want to prevent it from recurring, or are reaching their teenage years and starting to formalize and improve their processes and policies—risk management is generally top of mind for boards at this stage, especially if it was ignored during the start-up years.
Why WARGAMES?
Wargames—sometimes called decision games—are a time-tested means to evaluate your plans. Whether we’re talking miniatures skirmish games, script read-throughs, model UN, or the military decision-making process, decision games provide us way to assess goals in conflict without the cost of defeat.
If we’re going to practice cybersecurity, our goals are in conflict. Wargames give us a no-cost (or at worst, very low cost) way to determine if we are prepared, what we overlooked, what resources are missing, etc.
Plus, they’re fun!
I recently had the pleasure of traveling to the International Conference of Computing in Missions – Europe, where I delivered an eight-hour workshop on building cybersecurity programs. Basically, a dump of the core tradecraft I use when serving as a virtual chief information security officer.
At the end of the class, we spent two hours doing table-top exercises—wargames—with the class of about 25 attendees. The game not only served as a fun way to end a long day, but also as a means to:
Drive home the importance of incident response. Have you planned and prepared for emergencies?
Highlight the multi-stakeholder nature of cybersecurity. Sure, the IT and cyber staffs may *want* to pull the plug on a compromised system, but what does that mean for the business/organization and the customers—or even the computers?
Teach an evidence-driven approach to analyzing and responding to situations. That hypothesis sounds realistic, but where do you get the data to prove that’s what is happening?
Teach teams to listen and share expertise between exercise attendees. Is there something a new professional sees because he’s fresh out of school or something the old hat sees because she’s been in the trenches before?
They’re also a great way to exhaust your remaining brain power quickly!
If you set your goals and outcomes in advance, wargames can be as simple as sitting around a table talking through actions and taking notes—something our teams can all afford to do a couple times before we bother hiring a facilitator. The goals are normally to evaluate readiness or a specific plan, but you may not yet have a plan.
At risk of sounding like I’m describing a magic bullet, wargames can also help you build a plan. Even if you have a small team—or even if you’re flying solo!—challenge yourself with a small problem like, “a user in marketing had their username and password stolen!” What do you do?
The odds are, that your team already has an idea of what they’d do to respond. It just hasn’t been written down yet. At this point, the goal of the wargame is to capture the knowledge floating in each professional’s head so that the team can use it like a pre-surgery checklist in a real emergency.
Take turns talking through what each person would do in response to the problem. Make *everyone* talk when it’s their turn (introverts can conceal a wealth of knowledge).
Have a note taker write down the steps taken in response, whether right or wrong, in sequence.
After the game, ask which “steps taken” were effective and what resources were needed or missing. Keep taking notes.
Boil the list of steps taken down until it’s a simple checklist with broad steps (you can always add more details later).
Take action to start fixing resource gaps where you’re able to.
Wargaming is a flexible tool that doesn’t have to be expensive nor complicated. Hopefully this helps you figure out a few ways you can plug exercises into security, crisis response, and risk management processes!
Year in review
This year has FLOWN by! It's hard to believe it's already over... If you plan to donate to help us cover the cost of clients who need financial help in time for your 2023 tax return, please do so now!
Let's recap
Here are some of the creme de la creme highlights from what we got done this year:
Covered a missionary agency's security monitoring system for a month while the existing security staff took a much needed break
Built out a cybersecurity roadmap for a missionary team and for a health care provider
Revamped the cybersecurity policies for a major nonprofit helping alleviate poverty and homelessness
Taught six missionaries how to build-up their security posture during a one-day workshop at ICCM America
Helped a church spring-back in the aftermath of a computer breach
Returned to Europe to provide security hygiene checks to 60 missionaries
Wrote six "country studies" for missionaries deploying people and tech around the world
Made a vendor security questionnaire to help nonprofits with vendor risk management
Delivered countless gap assessments and made a self-assessment workbook
Spoke at two missionary conferences on integrating cybersecurity into missions
And that's without the day-to-day work included! Your support has propelled us forward through this year and we cannot say thank you enough!
Up next
We have lots planned for next year! We aim to:
Deliver another day-long training on improving cyber posture--this time at ICCM Europe in February
Design and deploy a secure travel network for our annual conference and security hygiene trip in Europe next September
Transform and improve our managed network monitoring system, which currently supports a couple campuses involved in anti-trafficking outreach and recovery
Convert as much of our 20 hours of existing training material into on demand classes as we can so that people don't have to wait on us to learn
Work with a business development professional to improve how we organize and talk about the business
Add SIX clients to our docket of on-going cyber support (we're currently at one--do you know anyone who needs support?)
Transform the team to drive towards long-lasting, repeatable impact
EOY giving and supporting operations in 2024
It's end of year giving season. If you plan to donate to help us cover the cost of clients who need financial help in time for your 2023 tax return, please do so by 31 December 2023.
We estimate that new operations in 2024 require we raise an additional $50,000 atop our currently pledged donations (we're predicting $16,000). If you or someone you know would like to donate to help, please do so here.
Thank you for all your continued support and prayers!
Turning the Course of Nonprofit Cyber
When talking to people about cybersecurity in the nonprofit space I frequently say, “The nonprofit sector is 15 years behind the power curve on cybersecurity.” I like to think that it’s provocative to say. But in all the times I’ve used it, I haven’t heard a single “Hey! That’s not fair!” in response.
Unfortunately, the nonprofit world is just waking up to this set of problems, and missionaries are no exception. So, let’s explore the drivers for security on the for-profit side of the house to see what lessons we can learn.
Drivers of Security
For-profit businesses have about 7 drivers that force them to confront cybersecurity and quickly get on top of it:
1. Breach – Getting breached and learning about breaches continues to be a major driver for business around the world. Paying the costs of a breach or ransom and going through all of the stress of recovering is pain that many prefer to avoid, so businesses build programs to prevent and respond to breach.
2. Insurance – Insurance providers have lost a huge amount of money to cybersecurity failures because of miscalculated risks. They are increasingly passing on the costs of breach to the insured company either in the form of high deductibles or high premiums—or refusing to issue a policy altogether—so establishing a cybersecurity program directly saves businesses money on their insurance policies.
3. Mergers, Acquisitions, Private Equity, and other Investors – Investors of all forms from seed funding to growth equity want to know that businesses are exercising due diligence and managing risk responsibly because they don’t want (overly) risky investments. Funding sources increasingly expect a minimal level of security and compliance before releasing funds, so businesses invest in cybersecurity to unlock more funding.
4. Board Members – As board members move from company to company, they take their lessons learned with them and their scar tissue. Businesses invest in cybersecurity to exercise their fiduciary responsibilities and keep the board satisfied.
5. New Customers – Customers have been burned by bad vendors in the past when service providers have failed to properly store private information or when data has been lost and disclosed in a breach. As customers (particularly for business-to-business products) begin to question vendors’ security postures and demand certain security features, businesses adapt so that they can close bigger deals.
6. Vendors – Security vendors constantly (cold-)call potential customers looking for new business. Security vendors play a minor role by ensuring that no one can forget about the problem and producing most of the content about fixing security deficiencies.
7. Compliance – Governments, industries, and professional organizations set standards which businesses must comply with. Compliance forces businesses to at least acknowledge the security problem, even if businesses are still often willing to bear the cost of a fine rather than investing in top-tier security.
Application to Nonprofits
I would argue that all of these can be drivers for nonprofits as well, but there’s work to be done to unlock each driver.
1. Breach – High-profile breaches like Blackbaud and SiteStacker are bringing awareness to nonprofits about risks to and via their donor management platforms. Ransomware spares no one. Attackers will drain a nonprofit or church’s bank account just like anyone else.
2. Insurance – Many nonprofits already rely on insurance in other domains, so insurance is already a viable driver for cybersecurity adoption across the nonprofit sector. The desire to get insured in case of breach or to drive the cost of insurance down may help bring up the level of security investment.
3. Mergers, Acquisitions, Private Equity, and other Investors – Grantors and foundations play this role in the nonprofit sector but I argue that they aren’t yet working to help nonprofits improve their cyber efforts.
4. Board Members – As experienced board members serve on multiple nonprofit boards, the number of boards that ask executive directors “What are we doing about cybersecurity?” will increase.
5. New Customers – It’s possible (though unlikely?) that mass movements of donors and supports will refuse to support a nonprofit if due diligence isn’t in place to prevent loss of money to cyberattacks. It’s more likely that the nonprofits themselves will push THEIR software vendors to improve to get ahead of third-party risk in a process that looks more like enterprise sales. Which is why we wrote a vendor security questionnaire.
6. Vendors – Security vendors can learn to speak “nonprofit”—and many are! (We’re one of them!) The advantage of traditional cybersecurity vendors is scale: having a large base of customers maintains a demand for high-quality output and actually drives prices down, making it more within reach for budget constrained organizations of all types.
7. Compliance – Governments, industries, and professional organizations set standards which businesses must comply with. Nonprofits are just businesses with a different fiduciary responsibility, so compliance can help drive adoption too. Since most mission-driven teams have some level of budget constraints, it’s less likely we’ll see them behave like multi-national banks who can eat a fine and more likely we’ll see proactive work to avoid fines.
Frameworks for Cyber Success
Nonprofits continue to lag on cybersecurity. Can frameworks help drive mission-driven cyber?
Cyber continues to lag in mission driven spaces.
I read a few stats from Diligent this morning that reminded me just how much cybersecurity matters in the mission driven and nonprofit space.
Here are a few from their "Key Stats that Boards Need to Know:"
50% of NGOs reported cyberattacks in 2021
NGOs and Nonprofits raise $30 BILLION each year
Only 25% of nonprofits monitor their networks
Only 20% have a cybersecurity plan
Clearly there is more need than the cyber industry is able to provide for!
Let's get into the weeds a bit on how Ericius Security helps fix this.
Frameworks for success
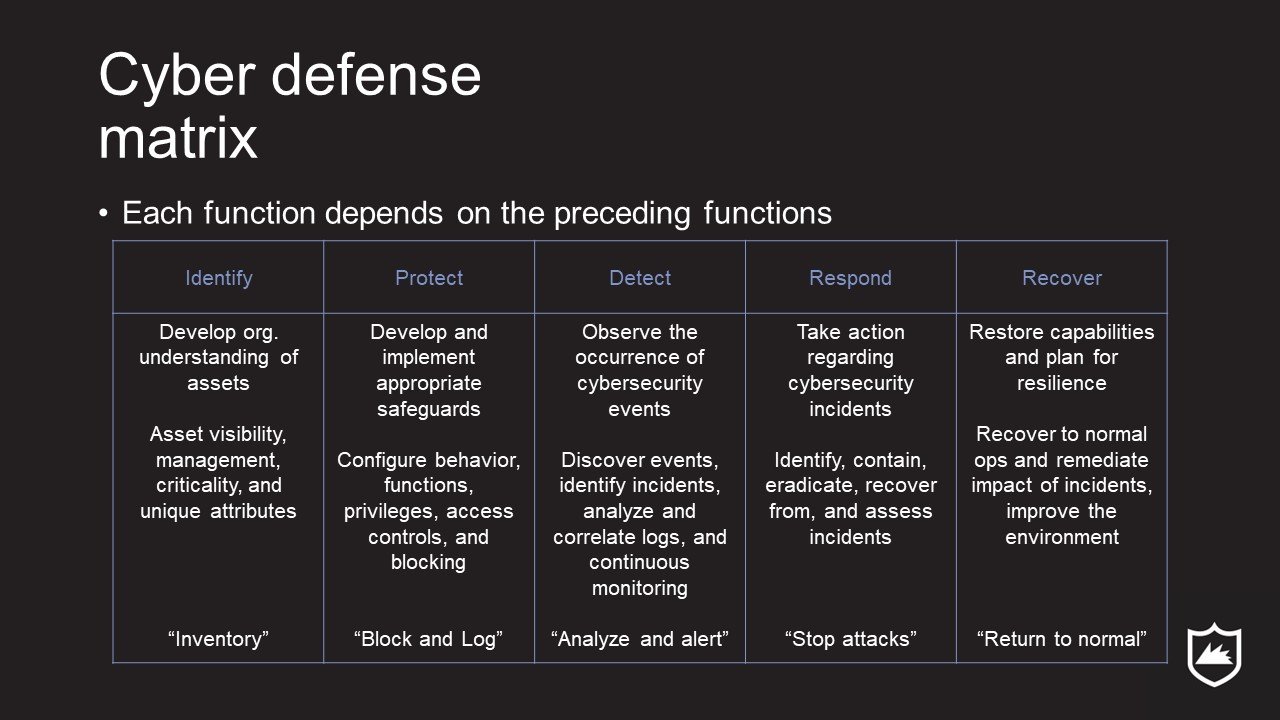
There are a number of good cybersecurity frameworks for organizing defenses and IT risk management. The CIS Critical Security Controls and ASD Essential 8 are popular, but I tend to lean on the National Institute of Standards and Technology's Cyber Security Framework (CSF) crossed with the Cyber Defense Matrix (CDM) by Sounil Yu.
Why? The CSF is free. You can use it commercially, so you can apply it to your business. And it's thorough enough to handle organizations of all maturity levels.
I cross it with the CDM to standardize the application of the CSF's functions across all types of IT assets, as well as to get a FAST representation of where a business's cyber program is at--two things that the CDM was specifically designed to do and does EXCEPTIONALLY well.
The CSF Provides the functions:
The five functions of the NIST Cyber Security Framework
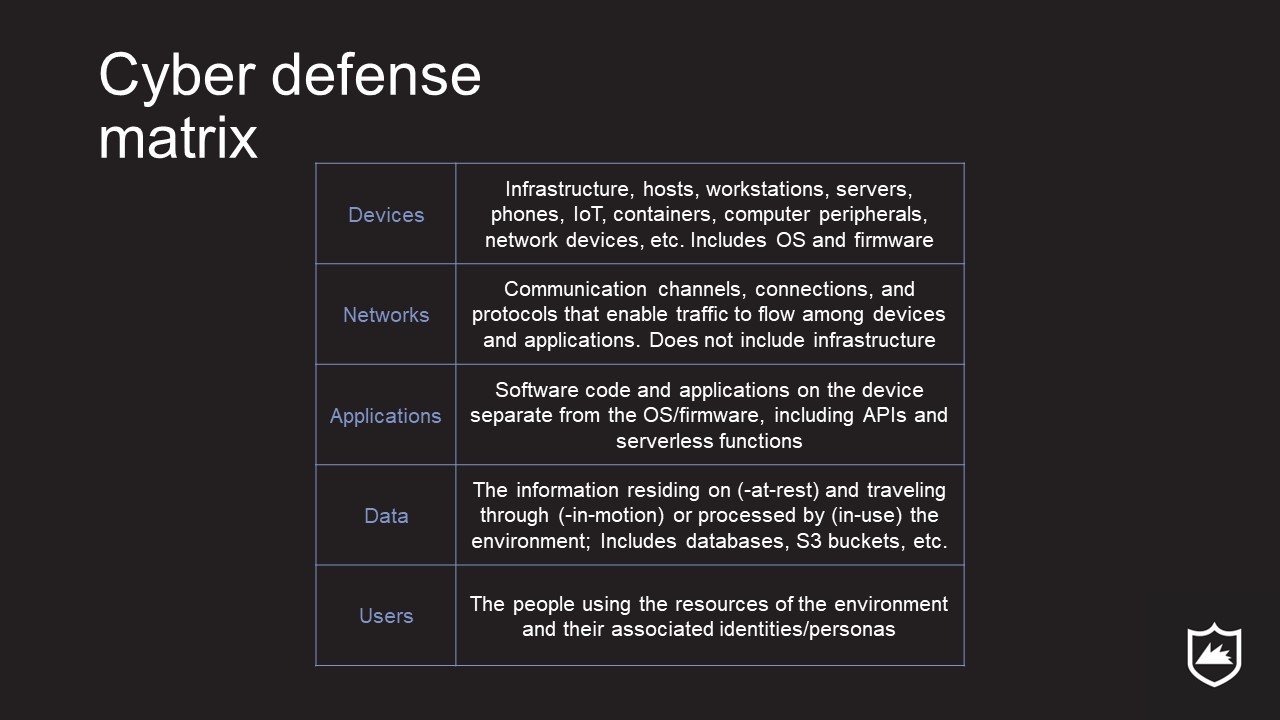
The CDM standardizes the functions across five assets:
The five asset classes as defined in The Cyber Defense Matrix by Sounil Yu
The resulting matrix allows us to produce a high-level view of the security program.
The cyber defense matrix
Here's how it works when I run it:
Discovery - We talk through the business's goals followed by everything in the existing IT environment. What needs defending? How many users are there? How are finances supporting the mission? Where are the pain points?
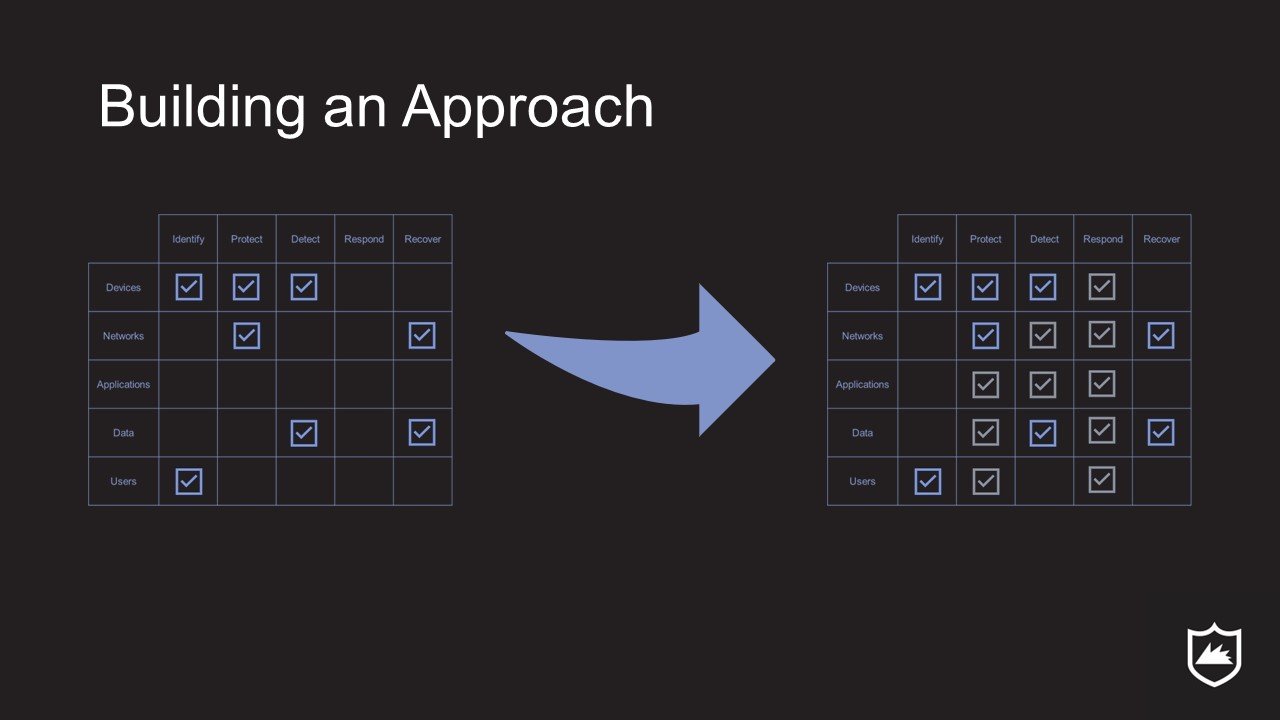
Map Current State - We map the existing defensive capabilities onto the CDM
The current state maps your existing cybersecurity capabilities to the cyber defense matrix
Map Desired State - We map the business's goals onto the CDM and define requirements, then we provide some professional insight about noticeable gaps, opportunities for improvement, and places where complexity can be reduced
The desired state overlays new cybersecurity capabilities on existing capabilities
Develop an Approach - We design a 3 steps bridge from the current state to desired state that the business can execute over the next year
The approach moves the current state to the desired state
Afterwards, we can either search for managed security services to fill gaps with the business, or we can do more detailed analysis, consulting, and program building--perhaps policies need to be written or a three year roadmap for growth needs to be designed.
If that sounds helpful to you or to a mission driven business you know, we've wrapped this all up in a DIY version that you can find here or you can always book a call to get help.